Hybrid IdP tenant configuration
Hybrid IdP tenant configuration
Learn how to configure a hybrid IdP on a tenant.
The following sections use three different roles to explain the process:
Steps for Kyndryl Admin
To provision a new tenant on MT environment:
- Log in to Core as a Kyndryl Admin at https://master-stage-core.multicloud-ibm.com/platform/tenants
- Click+ Create Tenant. The Create Tenant page displays.
- Complete the following fields:a. Customer Name: The name you want to use for the customer (for example, demo-customer)b. Enter Tenant Hostname: You can use the customer domain name (for example, demo-customer.multicloud-ibm.com)c. Enter Customer Email: Kyndryl Customer Admin Kyndryl IDd. Enter Kyndryl Client ID: Kyndryl Customer IDe. API Host URL: The URL will be populated automatically once you enter the Tenant Hostname. It is the API server addressf. Choose an Identity Provider: SelectIBMIDfrom the dropdown listg. Choose a Database Connection: Selectdefaultfrom dropdown list
- Under Applications, click the checkbox besideIBM Multicloud Core Plus.
- Selectcoreplusfrom the Choose Connection Type dropdown list.
- ClickCreate.
- When the page refreshes, check the tenant status by entering the tenant name in the text box.
Provisioning the tenant will take approximately 5 to 10 minutes. Once the tenant is provisioned successfully, an email invitation will be sent to the Kyndryl Customer admin email entered in step 3c above.
Steps for Kyndryl Customer Admin
In order to perform these steps, you need the email invitation sent to you by the system (see above). To add the identity provider:
- ClickGet Startedfrom the email.
- Enter your Kyndryl ID log-in credential and clickContinue. The privacy statement screen displays.
- ClickIBM Privacy Statementand read the document.
- ClickI Accept. The Kyndryl Modern Operations Applications welcome screen displays with your user name and role(s).
- Verify that the System Admin role is displayed beneath your name.
- Change the current url https://demo-hybrid8.multicloud-ibm.com to https://demo-hybrid8.multicloud-ibm.com/platform
- ClickSettingsand selectIdentity Providersfrom the list.
- ClickAdd Identity Provider. The Add Identity Provider window displays. Fill in the following:a. SelectSAML2.0.b. Name: Enter the name of Identity Provider (IdP) you want to see when you try to log in to your tenant.c. App Federation Metadata: SelectURL.
In order to perform the next steps, you will need to have the App Federation Metadata URL and User Claim Mappings. If you do not have them, ask for them from your Customer IdP Admin.
- In the list below, click the link corresponding with the Identity Provider that you are adding. Follow the instructions, and then return to the next step (that is, Save the User Claims Mappings to a file).
- Okta Config: Configuring Okta IdP https://confluence.gravitant.net/display/Eng/Configuring+Okta+IDP
- Azure IdP: Configuring Azure IdP https://confluence.gravitant.net/display/Eng/Configuring+Azure+IDP
- Save the User Claims Mappings to a file. You will need to upload that file later.
- Using the data in the App Federation Metadata URL and User Claim Mappings, fill in the text fields and other data options on the Add Identity Provider Page.a. Invitation Options: SelectDisable Email Invitations
- ClickCreate. The new IdP is added to the list of Identity Providers.
- Ask the Customer IdP Admin to login to the tenant (https://demo-hybrid8.multicloud-ibm.com/platform/) by clickingSign in with okta.
- Sign in as an Okta user who is a member of the Okta group (for example, Admin). This is required for a later step to create and configure hybrid mapping. At this point, the Okta user (Customer IdP Admin) has no associated roles and cannot perform any operations.
- Log in as Customer IdP Admin.
- As the Kyndryl Customer Admin, assign the newly added user to the Okta User tenant and to the INITIAL-SYS-ADMIN team so it will have the System Admin role.
- Click the Main menu on the upper-left corner of the page and select Admin and then User Access from the dropdown list.
- Go to Teams.
- Click on stocked bullets icon on the far-right end of the row of the team that you want to work with, and selectView Details.
- Scroll down to the Assign User(s) text box.
- Click the down arrow and select the newly added Okta user (Customer IdP Admin).
- ClickAssign.
Steps for Customer IdP Admin (Okta user)
To create the Auth Config document and Mapping to IdP using Developer Console:
- Logout and log back in. Now the System Admin role is activated.
- Click the user icon in the upper-right corner of the screen and select Developer Console. The Developer Console displays the API Documentation tab. (If not, click the API Documentation tab.)
- Selectcorefrom the Application dropdown list andcb-core-authorization-servicefrom the Service dropdown list.
- Locate "API - POST/core/authorization/v1/authtype/configurations" for adding the auth config.a. ClickTry it outand modify the payload as follows. Set the initial team code:
- initial_system_admin_team_code: Team code to be set
- initial_system_admin_org_code: Organization code for your Kyndryl Modern Operations Applications team
- initial_system_admin_team_external_ref_id: Set this to the Group name Okta, or, if for another IdP, the user of that IdP belonging to that IdP. For example: Okta user belonging to the Admin Group.
- auth_type: Hybrid
- name: Any name to identify
For example:
{ "initial_system_admin_team_code": "KyndrylAdmin", "initial_system_admin_org_code": "admin_org", "initial_system_admin_team_external_ref_id": "Admin", "auth_type": "hybrid", "name": "oktahybrid" }
- ClickExecute. The Response Payload is created. Take note of the ID from the response payload as it is needed in the next step.
- Optionally check if the team got created by selectingUser Accessfrom the Main menu dropdown list. Then selectTeams. The team created as KyndrylAdmin with System Admin Role should be in the list.
- Back in the API in the Developer console, locate POST/core/authorization/v1/configuration/idp.
- Create the mapping between IdP and authtype_config.
- ClickTry it outand modify the payload as follows. The value forauth_type_idis the value of the id that you took note of in step 1, above.{ "auth_type_id": "5e78f90143aea39e54d7c885" }
If successful, the response payload will be as follows. IdP ID is mapped to Auth Config ID.
Configuring IdP response payload
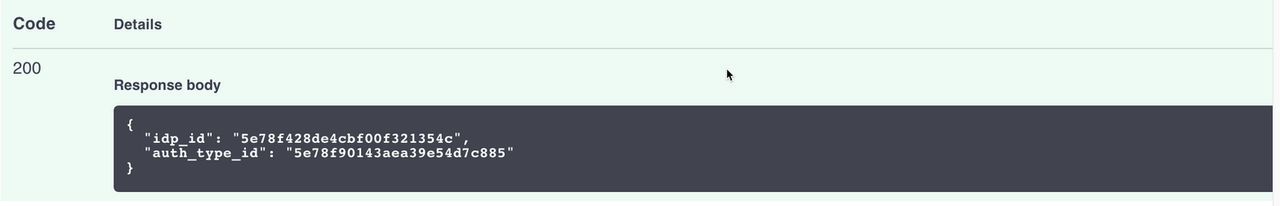
Okta IdP is configured as Hybrid.
- Log out and log back in as Okta user (Customer IdP Admin) using the Okta login credentials.
To assign a different role to other Okta users, create a new team in the Kyndryl Modern Operations Applications with that Role and enter the group name to which those users will belong as a value for the field external_reference_id.
Do you have two minutes for a quick survey?
Take Survey